The Three Components of a Security Risk Assessment
October 12, 2020
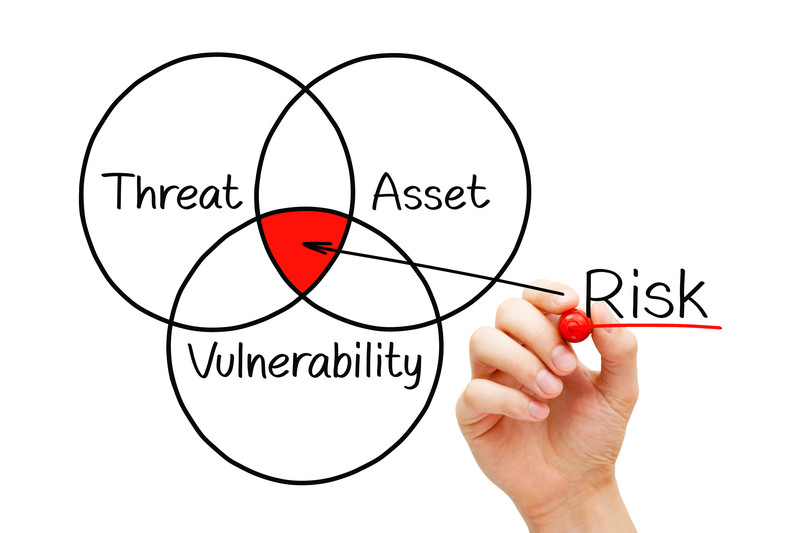
Threat, Vulnerability and Risk
What is the Best Way to Determine if Security is Adequate? A Security Risk Assessment.
More and more organizational leaders and Boards of Directors are asking the question, “is my security adequate?” To that question, one can only respond with another question, which is “adequate for what?” In our personal lives, if we want to know what is wrong with us, we will visit a doctor to be checked out or, as a minimum, have periodic evaluations of our general health. What would your reaction be, if without any testing or diagnosis whatsoever, your doctor suddenly informed you that you needed a serious operation? You would question why a conclusion is being drawn without an investigation and rightfully so! Similar philosophy should be applied to your security program. Significant changes to your security should not be implemented without the proper diagnosis called the risk assessment. As you read this article, can you produce the proof or articulate to your leadership or Board of Directors that you have identified and addressed the most likely security risks associated with your critical assets? This article will provide key definitions and demonstrate that the terms, “threat,” “vulnerability” and “risk” are not interchangeable. I will discuss various methodologies to help you get the desired outcome of a security analysis. While there are many ways to assess security, none are more effective than the comprehensive risk assessment that considers all three elements of risk as shown below.
Risk = Threat + Consequence + Vulnerability
Risk in this formula can be broken down to consider the likelihood of threat occurrence, the effectiveness of your existing security program, and the consequences of an unwanted criminal or terrorist event occurring. Here are some basic definitions to clarify the parts of the formula and the variations in outcome which occur if any portion of the three-part analysis is omitted.
Threat – a criminal or terrorist event which can have negative consequences on a critical asset. Critical assets can typically be put into several categories:
- People
- Property or Monetary
- Continuity of Operations
- Intellectual Property
- Reputation
Threats to people might take the form of workplace violence, with or without a weapon, from a variety of sources which are further defined elsewhere (view our page on workplace violence prevention) and will not be described in detail in this article.
Vulnerability – The next part of the risk assessment addresses vulnerability or “effectiveness of security”. Vulnerability is synonymous with susceptibility or weakness in an organization’s ability to prevent an attack against a critical asset.
Consequence – Consequence can be viewed as the degree of negative impact an incident would have if it were to occur. The table below shows an illustration of how one might develop a consequence model for an organizational security risk assessment. While the people safety consequence dimension is easy to define, the other consequence dimensions are very personal to each organization and will have to be determined at the onset of a security risk assessment.
A consequence model for injury to personnel is shown below from most to least significant:
- Fatality
- Hospitalization
- Lost time injury
- First Aid
- No injury
Organizations will need to develop their own models for other dimensions of consequence such as financial as $100,000 to one company may be catastrophic to one organization while for another it may be less than an insurance deductible.
When planning a risk assessment, the easiest way to define threats for your organizational audience is to translate threats against critical assets in the form of a defined scenario. That scenario then becomes the risk that you will assess in your risk assessment. For example, “a receptionist is injured by an irate customer in the lobby.”
Determining the Threat Level – Using the risk formula, you will start by determining the likelihood of the receptionist being attacked by an irate customer. This will involve studying previous security incident history and considering the nature of the business. For instance, if the organization is a law firm that deals with foreclosures, one might conclude that outsiders impacted by losing a home may come to the office angry, thus increasing the likelihood of a physical attack.
Vulnerability or determining the effectiveness of security – Properly identifying vulnerability requires a baseline knowledge set about what constitutes an effective physical security posture against common threats. This suggests that a certified security professional might be engaged when conducting a security risk assessment for better results, but it is not essential. Whenever an organization takes a systematic look at threats, vulnerability and consequences, it is better than guessing or being unduly influenced by a vendor promoting products.
So, what happens when you begin to do something less than considering all three elements of the risk formula? What follows is a description of risk management methodologies with a graphic to show what is considered versus what is omitted from consideration.
Threat Assessment – If you want to simply study the criminals or terrorists who may have an interest and create security problems for your organization, you might start with a threat assessment. This will encompass a study of only the first part of the formula as shown below.
Risk = Threat + Consequence + Vulnerability
Threat Assessment Focus
Vulnerability Assessment – Many counter-terrorism initiatives mandated by the US government are called vulnerability assessments. A vulnerability assessment will consider only two of the three elements of the risk formula. The threat level will be assumed to be at the highest level, and the organization will be forced to simply improve their security effectiveness by reducing vulnerability and find ways to reduce consequences which might include enhancing emergency response or developing business continuity plans. A vulnerability assessment typically results in excessive spending on security as the actual threat level and probability of incident occurrence is omitted from consideration.
Risk = Threat + Consequence + Vulnerability
Vulnerability Assessment Focus
Business Impact Analysis –A business impact analysis is another common methodology used in some organizations to identify the most critical of assets and build resiliency around those assets, often in the form of business continuity plans. Business Impact analyses may not consider threats or vulnerability and again result in spending that might not otherwise be indicated if the full spectrum of risk is considered.
Risk = Threat + Consequence + Vulnerability
Business Impact Analysis Focus
Security Audit –A security audit is probably the easiest methodology to execute as it is simply a verification that all security measures which are supposed to be in place are in fact in place and functioning correctly. The security audit will focus on the effectiveness of security or determine that vulnerability is being properly mitigated. The security audit certainly has its place in the analysis landscape, but it is not an assessment of risk and is unlikely to identify unknown vulnerability.
Risk = Threat + Consequence + Vulnerability (or effectiveness of security)
Security Audit Focus
In closing, there are several different security assessment methodologies. Hopefully, it is clear from this article that the terms “threat,” “vulnerability” and “risk” are not synonymous and cannot be used interchangeably. The most effective means of determining security adequacy is to consider all three elements of risk – threat, vulnerability and consequence. Risk assessments should be the methodology of choice if you are seeking to determine your security adequacy and avoid the potential pitfalls associated with failing to meet the expectations of the OSHA General Duty Clause or a successful claim against you under premises liability tort law. For more information, view our page on these terms and the physical security risk assessment process.


